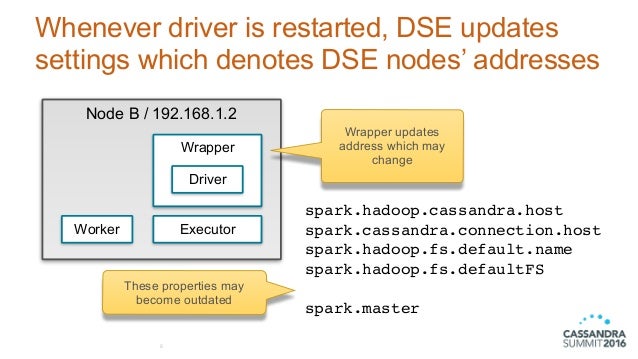
Acer Drivers Update Utility For Windows 7 is a program that updates your Windows 7 drivers for Acer devices automatically. Acer Drivers Update Utility. A program that updates your Windows. Scanning Engine (DSE). SONY Drivers Update Utility. As of January 2020, DataStax merged all of the DSE drivers functionality into the existing OSS drivers and all new features will be developed in the OSS drivers going forward, both for Apache Cassandra and DataStax Enterprise. Bug fixes for the DSE drivers will continue to be addressed until January 1st, 2022. This new version of the DataStax. 1: DSE and OSS Driver functionality to be merged. Since 2016, DataStax has maintained separate DataStax Drivers for Apache Cassandra (OSS drivers) and DataStax Drivers for DataStax Enterprise (DSE drivers). Today, DataStax announced the unified DataStax drivers that merge all of the DSE drivers functionality into the existing OSS drivers. A driver for Apache Cassandra(R) 2.1+ that works exclusively with the Cassandra Query Language version 3 (CQL3) and Cassandra's native protocol versions 3 and above.
One of the obvious things about the Windows operating system for anyone actively working on its kernel security is that the Driver Signature Enforcement (DSE in short) is not effective and can be bypassed with relative ease by any determined individual. From a historical perspective, the “feature” was introduced in the 64-bit build of Windows Vista in 2007 and has been shipped with all 64-bit Windows editions since then. In essence, it was designed to prevent unsigned device drivers (or kernel modules in general) from being loaded and executed with ring-0 privileges. Consequently, it broke one of the fundamental Windows assumptions followed since the early years of the NT family – administrative privileges in the system would no longer be equivalent to the ability to run arbitrary ring-0 code, effectively introducing a completely new layer of privilege separation in the system.
Drivers De Nvidia
Soon after the change was presented to wide audience, the enforcement was spectacularly defeated by Joanna Rutkowska, who took advantage of the fact that users in the Administrators group had been granted access to raw disk data and thus were able to modify parts of the pagefile.sys swap file potentially containing paged-out ring-0 code, to later execute the injected payload by crafting a special kernel-mode request (IRP to the NULL.sys driver in that particular case). Joanna’s and Alexander’s presentation was titled IsGameOver() Anyone? and received quite a lot of media attention at the time (mid 2007), starting a global discussion regarding the sense and security implications of introducing the mechanism. As a direct outcome, Microsoft decided to address this particular attack by disabling user-mode access to raw disk contents, and later on follow up with additional page hash/signing implementation for the hibernation and swap files (thanks Alex!). Since five years ago, the mechanism hasn’t been publicly criticized or otherwise discussed anymore – perhaps everyone just got used to its existence and (in)effectiveness.
Although you can think of it in terms of an additional barrier that ring-0 badware developers have to face, it certainly isn’t considered a security measure. Despite the extra separation level, admin → kernel escalations are not of much interest to the overall community, given that administrative rights are by far enough to compromise a system and guarantee infction persistence (with the small exception of the ability to communicate with machine peripherals, e.g. in order to set up a MBR/VBR rootkit). Additionally, a number of kernel-mode Windows components and features created in the pre-Vista era relies on ultimate trust to the Administrators group on so many levels that I really doubt it is realistically possible to reliably separate the two privilege levels at this point without investing an incredible amount of resources to introduce significant changes into the many areas of current system design.
I don’t usually pay too much attention to admin → kernel escalations when I sometimes stumble upon them during my daily work. However, today I would like to showcase an interesting set of bugs that I accidentally noticed a few weeks ago while doing some unrelated research. The nature of these bugs visibly exposes how flawed the signature enforcement idea has been from the very beginning. So, to the point: all device drivers present in the default Windows installation directory (Windowssystem32drivers) are obviously digitally signed and thus can be freely loaded or unloaded, assuming administrative privileges. Performing any of the two operations upon most .sys files doesn’t lead to any interesting behavior; however, if you attempt to unload some of them – or even better, load them in ring-0 more than once – you might end up triggering various types of Windows bugchecks, some of them in the most interesting locations or contexts I have seen in a long time. It turns out that these otherwise high-quality kernel modules fail to properly recover from encountering an error during DriverEntry initialization, or have serious bugs in the DriverUnload routines, most likely assuming that they would never be used anyway. Depending on the exact edition of Microsoft Windows, you can find up to 10 device drivers that are affected by the described flaws (out of ~300, if you’re interested in the metrics) in a default system installation.
Keep in mind that a system crash in one of those drivers doesn’t necessarily imply that it can be successfully exploited and used to run arbitrary ring-0 code. For instance, both DriverEntry and DriverUnload routines are typically called from within the System process, one that is inaccessible from user-mode; therefore, any NULL Pointer Dereferences occuring there aren’t of much use as they will always result in a Blue Screen of Death. As you will see, a few of the reproduced crashes are more complicated and affect the system state as a whole (e.g. by corrupting the kernel pools), therefore, they are likely enough to subvert the Driver Signature Enforcement mechanism. Ironically, a feature that was bypassed using a fairly complex attack and argued over for a long time could have been defeated with just the default drivers shipped with every Windows out there… that’s fascinating :-)
Below are listed eight crashes that I have reproduced on a Windows 7 SP1 64-bit machine; additionally, there is one more case of a driver that only fails under the new Windows 8 operating system. For each discussed driver, you can also find a short explanation of the programming bug that led to the bugcheck. I’m intentionally not including reliable exploits for any of the issues. Some of them do seem like good exploitation candidates, though :) Have fun!
acpi.sys
Explanation
The crash occurs during the execution of acpi!DriverEntry – the driver’s entry point calls the hal!HaliInitPowerManagement import routine. From there, the call chain goes all the way to nt!HalpGetChipHacks residing in a special “INIT” section. Since the section is marked as Discardable through a IMAGE_SCN_MEM_DISCARDABLE flag in its Characteristics descriptor field, the corresponding physical memory is unmapped from virtual space as soon as it is no longer needed (that would be early stages of system boot). Consequently, loading acpi.sys driver at any time after the system is already up and running would most likely result in an attempt to execute an unmapped memory area, as shown in the above listing.
bowser.sys
Explanation
Long story short, the relevant, buggy piece of code within bowser!DriverEntry is represented by the following pseudo-code:
The driver tries to create a device with a fixed name and after returning from the IoCreateDevice call, it blindly assumes that the operation has succeeded; if it is the second instance of the module in the operating system, the assumption is broken, resulting in numerous dereferences of the NULL address treated as a device object pointer.
Diskdump.sys
Explanation
The traditional definition of a DriverEntry function is as follows:

Under normal circumstances, the second parameter contains a valid pointer into a string describing the driver’s registry path. For diskdump.sys, however, the semantics of the parameter are different; the kernel seems to use it as some kind of a shared structure, both read from and written to by diskdump.sys. In fact, one of the first operations executed by the routine is the following call:
That’s right – the driver ends up zeroing-out 65,536 bytes of the kernel pool area. After that happens, it doesn’t take more than a few seconds (usually far less) to see the screen being filled with blue pixels. Very difficult in reliable exploitation, but perhaps possible with the right degree of kernel pool massaging.
Dumpata.sys
Explanation Drivers kofax image products.
Similarly to Diskdump.sys, the Dumpata.sys driver appears to interpret the second parameter of DriverEntry differently from its typical meaning. This time, an internal IdeDumpPortInitialize function treats some of unicode string’s bytes as a virtual memory address and tries to access it… with no chance to succeed.
dxg.sys
Explanation
The dxg.sys executable imports several functions from the primary Windows graphical driver – win32k.sys. As the latter image resides in so called session memory which is only mapped in threads marked as GUI and the process of resolving dxg.sys dependencies takes place in a non-GUI System process, a fatal exception is raised upon trying to access the base address of the win32k.sys image. Qxcomm driver download for windows 10 32-bit.
dxgkrnl.sys
Explanation
Although a NULL Pointer Dereference, this case is particularly funny. The affected part of DriverEntry works in the following way:
Both routines operate on a shared structure pointed to by a global dxgkrnl!pDxgkSqmControl pointer. The pointer is initialized for the first time in the DxgkSqmInit function, therefore it is still equal to NULL at the time of calling DxgkSqmShutdown. The deinitialization proc doesn’t expect pDxgkSqmControl to be zero and simply starts destroying and cleaning up particular fields within the structure, which results in an unhandled exception at the first attempt of using the pointer in a memory operation.

ndis.sys
Explanation
The root cause of this NULL pointer dereference system crash is not clear; the case requires further investigation.
wimmount.sys
Explanation
Yet another failed attempt to recover from an error in DriverEntry. In case one of the external functions called there (e.g. FltRegisterFilter or FltCreateCommunicationPort) fails, the Unload routine is called. Unfortunately, it doesn’t care to verify which portions of the internal driver state have been successfully initialized before, and just destroys everything it knows of, eventually leading to usage of an unitialized NULL pointer.
Dell Drivers
rdyboost.sys (Windows 8 64-bit only)
Drivers De Sonido Windows 10
Explanation
Drivers De Hp
At startup, rdyboost.sys creates a new kernel thread in the system starting at the SmdRBMemoryWatchdogThread routine. The driver fails to properly terminate the thread during the DriverUnload clean-up procedure, consequently leaving an actively running thread within a memory area that has been unmapped by the kernel in the final stage of unloading the driver. As soon as the scheduler gets back to the dangling thread, an exception is raised due to an attempt to execute unmapped memory, as shown in the above listing.
